The risks due to cloud misconfiguration are generally acknowledged. 92 percent of respondents are concerned about these risks, and 82 percent reported security and compliance incidents resulting from them. The problem is so big, Gartner’s Neil MacDonald estimates that, by 2020, 80 percent of cloud breaches will be due to misconfiguration and human error.
Yes, cloud misconfiguration risk is real. But what's the cost of managing it?
That said, I’d like to take a moment to focus on a much less understood aspect of cloud misconfiguration: the cost of managing the problem. There just isn’t a lot of information out there on how much time and resources are devoted to cloud misconfiguration. It's what motivated us to conduct this survey.
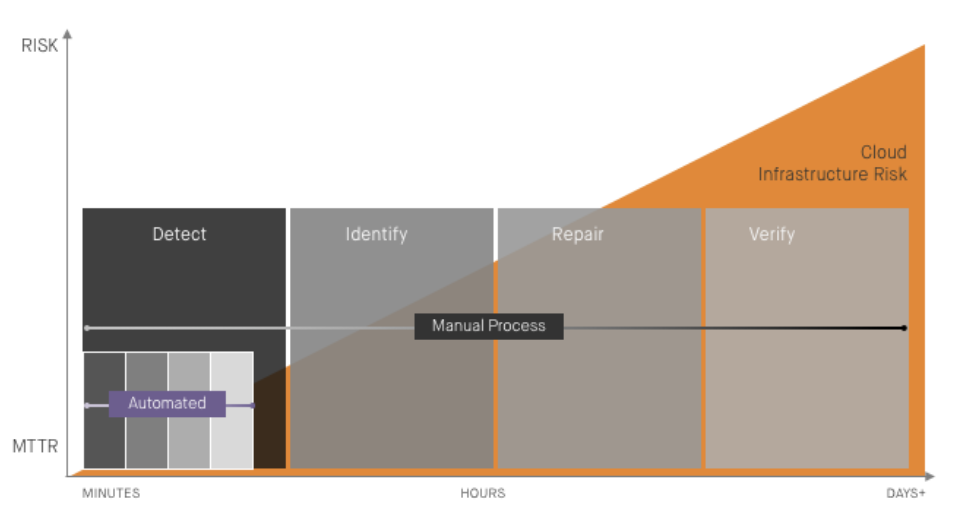
The cost of cloud misconfiguration stems from a lack of automation. The cloud is purpose-built for automation. API-driven infrastructure, continuous integration, provisioning, instance configuration, and monitoring are among the many cloud-based tasks that have been automated. Show me a common manual repetitive task in the cloud, and I guarantee you it’s been automated.
Cloud security is still largely a manual process
That is, with one glaring exception: infrastructure security. Cloud infrastructure needs to be provisioned according to a set of security or compliance policies, and once running, it must not drift out of compliance. Both of these tasks remain largely manual and error-prone. DevSecOps is on its way to addressing the former with automated policy-as-code validation of infrastructure. But when it comes to managing misconfiguration for running infrastructure (commonly referred to as configuration drift), the task is still predominantly manual--and costly.
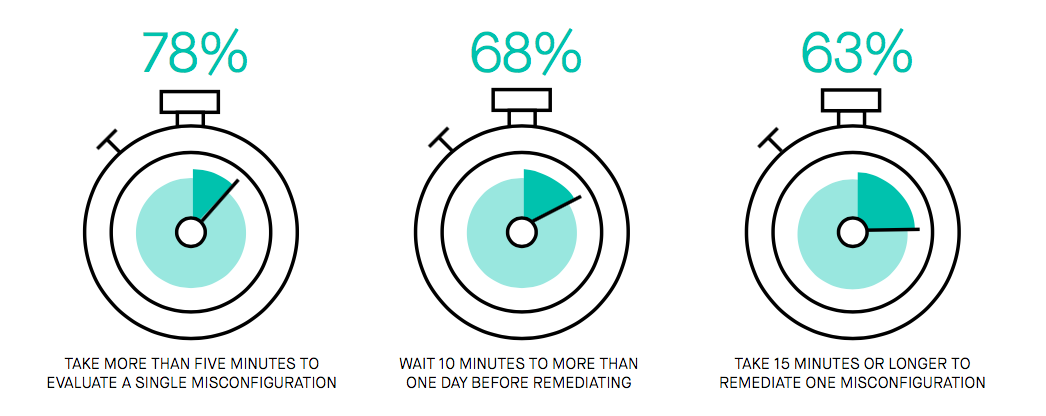
What do I mean by costly? I’m referring to the time it takes to:
- Review cloud misconfiguration alerts to identify critical events that require remediation (78% take five minutes or longer per incident)
- Manually remediate misconfigured resources (63% take 15 minutes or longer per incident)
- Producing reports on each misconfiguration (68% take 15 minutes or longer per incident)
These are all highly repetitive, manual, and error-prone tasks. You can read more about the manual processes involved in The Day in the Life of a Cloud Misconfiguration.
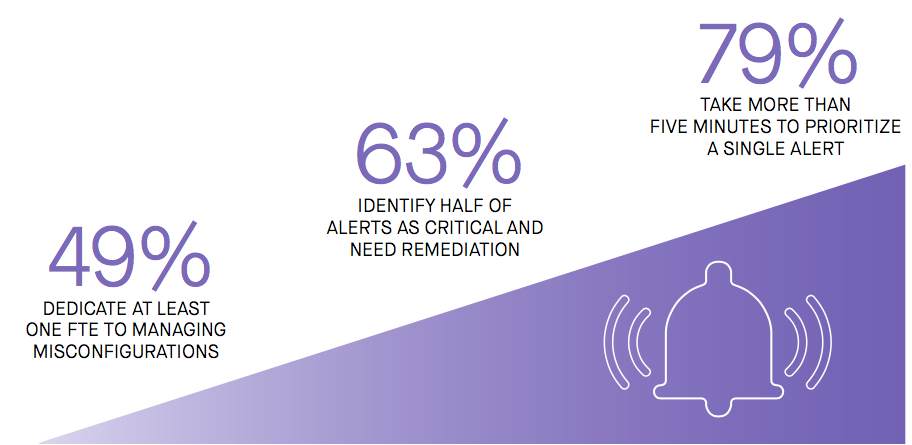
Management of cloud misconfiguration is costly
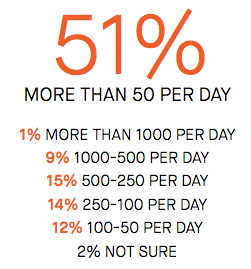
Factor in the frequency of misconfiguration and we have an expensive game of whack-a-mole. More than half of respondents reported a frequency of 50 or more misconfiguration events per day for the infrastructure their teams manage (64 percent manage 20 or more cloud-based workloads). That’s a lot of misconfiguration to identify and fix, and more than half of the teams surveyed dedicate the equivalent of at least one full-time engineer to the task. Multiply that across the average enterprise using cloud at scale, and you’ve got a lot of waste.
I think we’ve found a prime target for automation!
Security automation can bring efficiency gains
Thankfully, the survey’s respondents overwhelmingly point to the solution: automate the process of remediating misconfiguration. 75 percent said an automated remediation solution for cloud misconfiguration would improve efficiency, in addition to helping keep data safe (80%) and in compliance (79%).
It’s important to note that there are valid concerns about automated remediation for cloud misconfiguration since it can create alert fatigue and produce false positives resulting in bad changes and system downtime. That’s why it’s critical for an automated remediation solution to return misconfiguration to a known-good baseline established by the infrastructure team, as opposed to making changes independent of the baseline they establish.
Next week we’ll take a deeper dive into the risks of cloud misconfiguration and the insights the survey provides there. Until then, download our free Cloud Infrastructure Misconfiguration Report.
